Sipi’s methods of secure data destruction ensure your end-of-life IT assets are handled securely and efficiently.
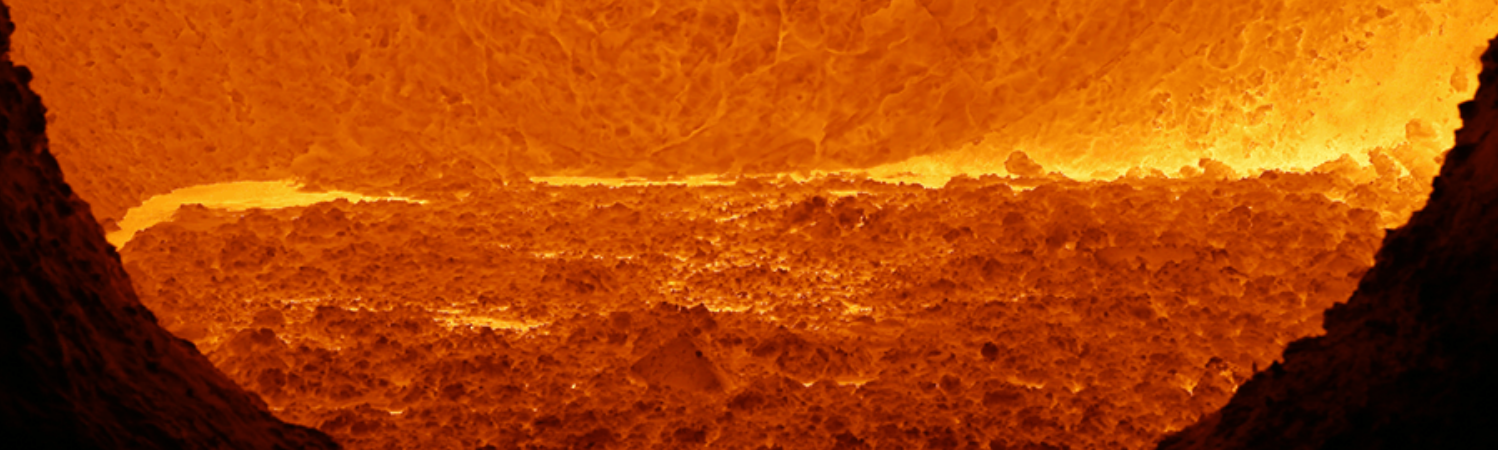
Sipi FIREMELT℠
Sipi is the only company to offer FIREMELT℠ — a data destruction service that guarantees 100% destruction for your organization’s most sensitive data. FIREMELT leverages Sipi’s unique history in metals utilizing a process that results in molten liquid that can then be poured into ingots and recovered.