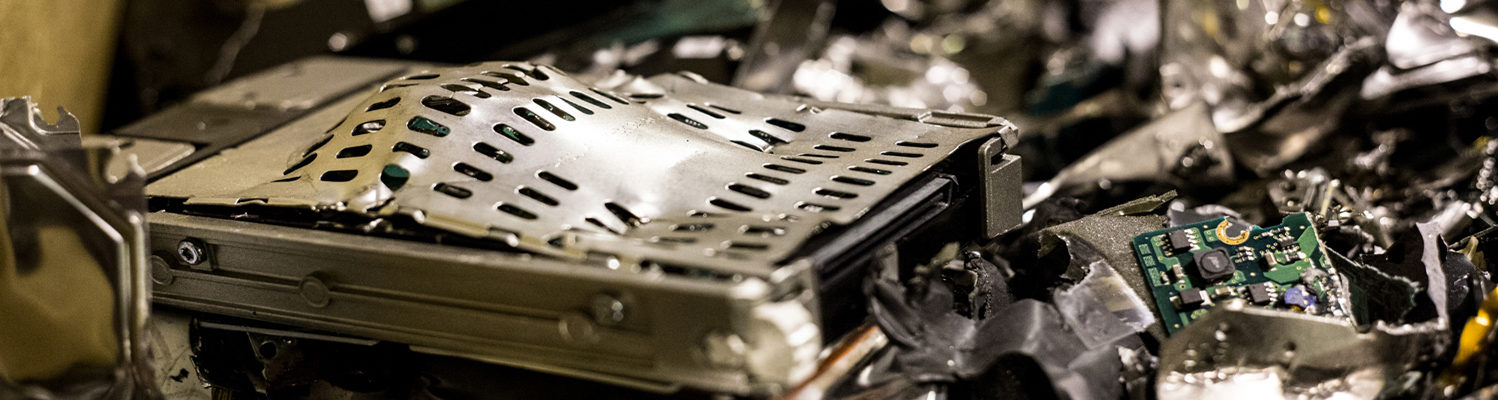
This method of secure data destruction employed by Sipi involves the shredding and crushing of the physical asset which contains the data. After this process is complete, it’s very difficult to recover any data from the device and goes a step beyond a data wipe – they’re quite easy to distinguish from a functional device. Shredding and crushing drives can save time and money, depending on the nature of the asset and its risk profile.
Here we answer the most frequently asked questions about this method of data destruction:
Drive Shredding and Crushing FAQ
Q: What does drive shredding and crushing entail?
A: Drive shredding and crushing is the physical destruction of a data-bearing asset via industrial sized shredders, manual/leverage crushers or automatic crushers.
Q: Which asset disposition issue does this address?
A: After an asset goes through either of these processes, retrieving any data from the device is extremely difficult. Drives that are destroyed in this manner are easily distinguished from non-destroyed drives.
Q: What are the missing elements or concerns with this method?
A: Unless either data wiping or degaussing has been competed prior to crushing or shredding, data still resides on the fragments or pieces of the asset that remain. This method makes obtaining the data very difficult, but it can still be accessed if technology, resources and time are not limiting factors. Both of these processes will produce particulate and dust, which will need to be addressed both during and after the destruction process. Any shredding or crushing solution will require a properly vetted downstream recycler.
Q: When and why would an enterprise use these methods?
A: Depending on the risk profile, an extra level of security can be helpful to further protect secure data or if a data-bearing asset cannot be wiped or degaussed. When destroying larger density drives such as HAMRs and MAMRs, the process often requires excessive amounts of time. Therefore, crushing and shredding these assets can save both time and money.